pfSense
Introduction to pfSense
In the world of firewall and router solutions, pfSense stands out as a versatile and powerful choice. It’s an open-source firewall/router software based on FreeBSD and can be installed on a PC or a virtual machine. It offers a range of features like VPN, security, routing, and load balancing, making it a comprehensive solution for both enterprise and home networks.
Why I Chose pfSense for My Home Network
I’ve always had a keen interest in exploring different networking tools and technologies. For years, I was a loyal user of Mikrotik Routerboard routers, which served me well, especially in terms of learning and experimentation. However, a recent upgrade to fiber internet, pushing speeds beyond a gigabit, necessitated a change. Mikrotik didn’t offer a viable option for these new demands. After some research, I decided to switch to pfSense. It was a toss-up between pfSense and OPNsense. If I were to do it over I would choose OPNsense but there doesn’t appear to be too much difference.
What to Expect in This Post
In this post, I’m going to dive into why and how I virtualized pfSense using Proxmox, the hardware setup (specifically the 4-port 2.5GB NIC), configuring pfSense, and integrating advanced features like Snort, pfBlockerNG, and Tailscale. I’ll also touch upon logging with Splunk, but that’s a big enough topic to deserve its own post.
Virtualizing pfSense with Proxmox
Originally starting as a small project, virtualizing pfSense with Proxmox quickly became the backbone of my home network. The new server setup and transition to pfSense was seamless. For more on my Proxmox journey, check out my previous blog post here.
The Advantages of Proxmox for pfSense
Running pfSense on Proxmox offers a host of benefits. The ease of creating backups and snapshots is invaluable, especially when experimenting with network changes. It allows for a flexible and forgiving environment where I can test new configurations without fear of breaking my network.
Hardware Setup
I opted for a 4-port 2.5GB NIC, primarily due to its affordability, at around $50. It was the perfect fit for my underutilized server.
Physical and Virtual Integration
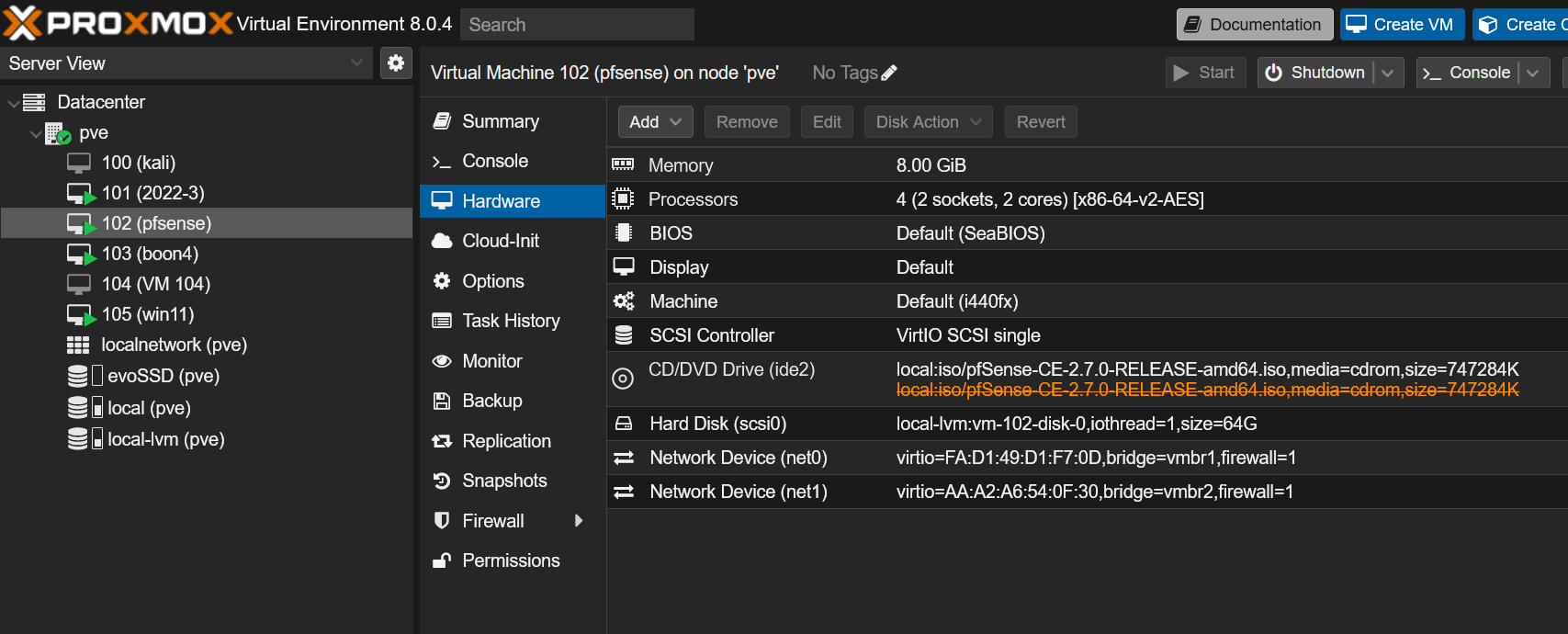
As detailed in my last post, the physical setup was straightforward. In Proxmox, pfSense is allocated with 8GB of memory, 2 sockets with 2 cores each, and utilizes bridged networks vmbr1 and vmbr2. Here’s a screenshot of the Proxmox -> pfSense -> Hardware setup for a visual understanding:
Setting Up pfSense
The setup process was surprisingly straightforward. Beyond selecting the WAN and LAN networks, I stuck mostly to default settings, and everything functioned smoothly. The out-of-the-box support for IPv4 and IPv6 was impressive, allowing me to delve deeper into understanding IPv6 without any initial hurdles.
Snort for Network Security
Snort, an open-source network intrusion detection system (IDS) and intrusion prevention system (IPS), is a key component of my network’s security. Hosting my own websites, like joshsisto.com, demands robust security measures. In pfSense, I’ve configured Snort with a balanced IPS policy, enabled all rule sets, and included mechanisms for port scan detection.
pfBlockerNG: From Pi-hole to pfBlockerNG
Transitioning from Pi-hole, pfBlockerNG in pfSense has been a revelation. It offers a comprehensive list of feeds for DNS level blocking, simplifying the process of keeping unwanted traffic at bay.
Tailscale Integration
I’ve been a fan of Tailscale for its simplicity and efficiency. Integrating it into pfSense was a breeze, and setting it up as an exit node has allowed for seamless connection to my home network.
Logging and Monitoring: A Glimpse into Syslog and Splunk
pfSense forms the largest source of logs for my Splunk setup. The insights gained from this data are invaluable, ranging from tracking blocked traffic to monitoring network connections. The setup was straightforward, involving directing system logs to Splunk via port 514. I’ll delve deeper into this in a future post.